State-sponsored cyber operations have become a central tool in modern geopolitical competition. Unlike criminal hacking, these operations are typically aligned with national interests such as intelligence gathering, strategic disruption, or signaling power without crossing the threshold of conventional warfare.
As digital systems increasingly control critical infrastructure, state-backed cyber activity has shifted from espionage toward influence and disruption. This article explains what state-sponsored cyber operations are, how they differ from other cyber threats, and why they are so difficult to deter or publicly confirm.
Quick Navigation
What Are State-Sponsored Cyber Operations?
State-sponsored cyber operations are activities conducted by government agencies or groups acting on their behalf. These operations may target:
-
Government networks
-
Military systems
-
Critical infrastructure
-
Strategic industries
They are often designed to remain covert, deniable, and below the level that would trigger military retaliation.
This strategic ambiguity plays a major role in incidents tied to critical infrastructure cybersecurity risks
How State-Sponsored Operations Differ From Cybercrime
Motivation and Objectives
Cybercriminals seek financial gain. State-sponsored actors pursue:
-
Political leverage
-
Strategic advantage
-
Intelligence collection
-
Long-term access to systems
These objectives shape how attacks are planned, executed, and concealed.
Resources and Persistence
Nation-state actors typically have:
-
Dedicated teams
-
Long-term funding
-
Access to zero-day vulnerabilities
-
Patience to remain undetected for months or years
This persistence allows them to infiltrate complex environments such as those affected by industrial control system security failures
Common Types of State-Sponsored Cyber Operations
Espionage and Surveillance
Many operations focus on quietly extracting data rather than causing disruption. These campaigns may target:
-
Energy sector designs
-
Infrastructure layouts
-
Incident response procedures
Such intelligence can later support more aggressive actions if needed.
Prepositioning for Future Disruption
Some state actors infiltrate systems without immediate impact, leaving access points in place for potential future use. This tactic raises concerns about latent threats within infrastructure environments.
Strategic Disruption and Signaling
In certain cases, cyber operations are used to:
-
Demonstrate capability
-
Apply pressure without escalation
-
Influence negotiations or public perception
These actions often blur the line between cyber activity and acts of state power.
Why Attribution Is Especially Difficult in State-Sponsored Operations
Nation-state actors are highly skilled at masking identity.
They commonly:
-
Use shared or stolen tools
-
Route activity through multiple jurisdictions
-
Mimic criminal or activist groups
This deliberate ambiguity directly contributes to cyberattack attribution challenges
The Role of Plausible Deniability
Plausible deniability is a core feature of state-sponsored cyber operations.
Governments benefit from:
-
Avoiding direct responsibility
-
Limiting diplomatic fallout
-
Maintaining strategic flexibility
This makes public confirmation rare, even when private confidence is high.
State-Sponsored Cyber Operations and Infrastructure Incidents
When infrastructure failures occur, state-sponsored activity is often suspected because:
-
Infrastructure targets carry strategic value
-
Disruption can create political pressure
-
Attribution uncertainty limits retaliation
However, not every outage is the result of hostile action, reinforcing the need to distinguish power grid failure vs cyberattack
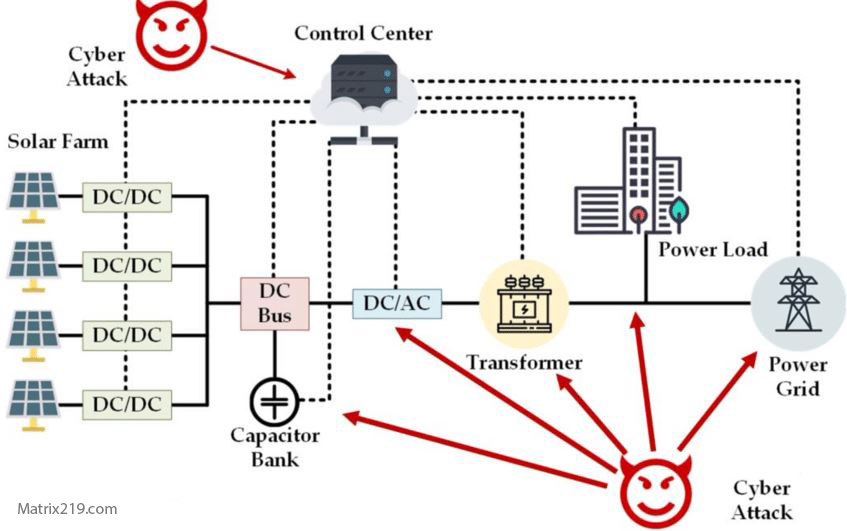
Defensive Challenges Against Nation-State Actors
Defending against state-sponsored threats is difficult because:
-
Attackers may already have access
-
Traditional security controls may be bypassed
-
Detection often relies on subtle anomalies
Defense strategies must prioritize resilience, monitoring, and response readiness rather than absolute prevention.
These principles underpin critical infrastructure cyber defense strategies
Why State-Sponsored Cyber Operations Are Likely to Increase
Several trends suggest continued growth:
-
Low cost compared to conventional military action
-
Difficulty of attribution
-
Limited international legal enforcement
-
Expanding digital attack surfaces
As infrastructure becomes more connected, cyber operations will remain an attractive instrument of state power.
Conclusion
State-sponsored cyber operations represent a strategic evolution in how nations project power and influence. Operating in the gray space between peace and conflict, these activities exploit technical complexity, legal ambiguity, and political caution.
Understanding how and why nations use cyber operations is essential for evaluating major cyber incidents objectively. Without this context, public narratives risk oversimplifying events that are inherently complex and uncertain.