Privacy vs Security is a comparison many people misunderstand, often assuming that the two concepts mean the same thing. While they are closely related, privacy and security address different problems and require different approaches.
Confusing privacy with security can lead to false confidence. A system can be secure but still invasive to privacy, and a private setup can still be insecure if basic protections are missing. Understanding the distinction is essential for making smarter decisions about tools, settings, and online behavior.
This article explains the difference between privacy and security, how they overlap, and why balancing both is critical in the modern internet.
Quick Navigation
What Online Security Really Means
Security focuses on protection against threats. Its goal is to prevent unauthorized access, data breaches, malware infections, and account takeovers.
Security measures include strong passwords, two-factor authentication, encryption, and system updates. These protections reduce the risk of attacks but do not necessarily limit how much data is collected or shared.
Security threats often originate from malicious actors rather than legitimate platforms.
What Digital Privacy Really Means
Privacy focuses on data collection and usage. It addresses how much information is gathered, who has access to it, and how long it is retained.
A platform can be secure while still collecting extensive user data for analytics or advertising. Privacy concerns arise even when no breach or attack occurs.
To understand how data collection works at scale, see: Digital Privacy and Online Tracking: How You’re Tracked Online and How to Protect Yourself
How Privacy and Security Overlap
Privacy and security overlap when protecting personal data from misuse. Encryption, for example, enhances security and supports privacy by preventing unauthorized access.
However, overlap does not mean equivalence. Strong security does not automatically imply strong privacy, especially when data collection is extensive.
Understanding tracking technologies helps clarify this distinction, as explained in: How Websites Track You
When Security Can Harm Privacy
Some security measures increase data collection. Monitoring systems, logging, and behavior analysis can improve security while reducing privacy.
For example, fraud detection systems may track user behavior extensively. While these systems improve safety, they can also create detailed user profiles.
Knowing who controls collected data helps evaluate this trade-off, as outlined in: Who Collects Your Data Online
When Privacy Can Affect Security
Extreme privacy measures can sometimes weaken security. Disabling updates, avoiding identity verification, or using unreliable tools may reduce visibility but increase vulnerability.
Balanced privacy strategies aim to reduce unnecessary data exposure without compromising essential protections.
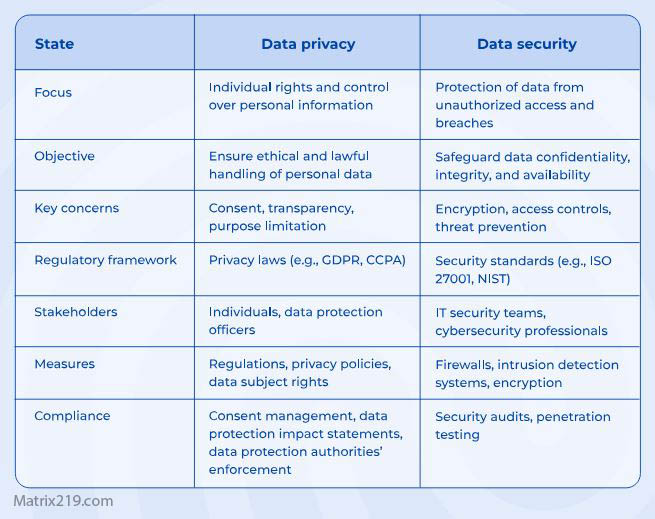
Privacy vs Security
Choosing Tools With the Right Balance
Effective digital protection requires evaluating both privacy and security aspects. Tools that prioritize one while ignoring the other often create gaps.
Understanding how apps and services collect data helps users assess this balance more accurately, as covered in: How Apps Track You
Practical Balance Between Privacy and Security
The most effective approach combines strong security practices with privacy-aware behavior. This includes securing accounts while limiting unnecessary data sharing.
Practical steps to reduce tracking without harming security are explained here: How to Stop Online Tracking
How to Stop Online Tracking
FAQ
Is security more important than privacy?
Both are important. Security protects against attacks, while privacy limits unnecessary data exposure.
Can a secure service still violate privacy?
Yes. Security does not prevent extensive data collection or sharing.
Does improving privacy weaken security?
Not necessarily. Balanced approaches can enhance both.
Are privacy tools also security tools?
Some overlap exists, but many tools focus primarily on one area.
What should users prioritize first?
Basic security first, followed by privacy-aware adjustments.